Public Policy
In the rapidly evolving digital landscape, cybersecurity has become a critical issue that impacts national security, economic stability, and the privacy of individuals. Public policy on cybersecurity aims to address these challenges by establishing frameworks, guidelines, and regulations that protect information systems, networks, and data from cyber threats. Effective public policy must strike a balance between innovation, privacy, and security while fostering collaboration between governments, businesses, and individuals.

Recent Highlights
Cloud Security Challenges in a Multi-Cloud World
The x86 wish list: Complexities of an imaginary Intel takeover
The Rise of Quantum Computing and Its Impact on Encryption
The Evolution of Artificial Intelligence in Cybersecurity
Quantum Computing: The Future of Superfast Problem Solving
Computer Access Laws.
Laws restricting computer access and use should carefully balance the need to combat cybercrime with the value of supporting security research, innovation, and other legitimate activity.
International Trade and Exports.
Cybersecurity is a global effort that depends on the free flow of information across borders. Trade agreements and export controls should aim to boost security without imposing overbroad restrictions on global data flow.
Vulnerability Disclosure and Incident Reporting.
Organizations are increasingly expected to disclose, receive, and act on information about cybersecurity incidents and vulnerabilities. Techsecur3 works to ensure these requirements are harmonized and flexible, and that they avoid creating new opportunities for cyberattacks. a little bit longer and forget all this nonsense.
Securing Data and Systems.
-
-
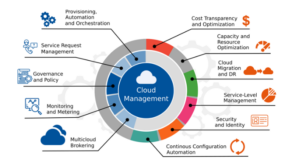
Cloud Security Challenges in a Multi-Cloud World
Read MoreThe rise of multi-cloud strategies has revolutionized how businesses manage and deploy their applications, data, and workloads. By leveraging multiple cloud providers, companies gain flexibility, avoid vendor lock-in, and optimize costs. However, this approach also introduces a complex set of security challenges that require careful
-

-

The x86 wish list: Complexities of an imaginary Intel takeover
Read MoreApparently AMD has blocking rights for any acquisition of Intel. If a deal were to happen, what would AMD ask for? The x86 architecture has been the backbone of computing for decades, powering everything from personal computers to data centers. But what if, in a twist
-

-

The Rise of Quantum Computing and Its Impact on Encryption
Read MoreIntroductionQuantum computing has the potential to solve some of the world’s most complex problems but could also pose one of the biggest threats to cybersecurity. Traditional encryption methods that secure sensitive data today may be rendered obsolete as quantum computers become capable of breaking these
-

-
The Evolution of Artificial Intelligence in Cybersecurity
Read MoreIntroductionArtificial Intelligence (AI) is reshaping the cybersecurity landscape with unprecedented speed. Cybersecurity, once dependent on manual rule-based systems, is now leveraging AI to stay ahead of complex and rapidly evolving threats. With cyberattacks growing in sophistication and volume, AI presents a powerful tool to enhance
-

-
Quantum Computing: The Future of Superfast Problem Solving
Read MoreIntroduction: Quantum computing is rapidly emerging as one of the most exciting and transformative technologies of the 21st century. Unlike traditional computers that process data in binary (0s and 1s), quantum computers use quantum bits or "qubits," which can represent multiple states simultaneously. This allows
-

-

Li-Fi: The Next Generation of Wireless Connectivity
Read MoreIntroduction: Imagine a world where your internet connection is not transmitted through radio waves but through light. That world is closer than you think, thanks to Li-Fi (Light Fidelity) technology. Li-Fi uses visible light communication (VLC) to transmit data, offering faster, more secure, and interference-free
-

-

The Rise of 6G Technology: A New Era of Connectivity
Read MoreIntroduction: As the world is just beginning to experience the full impact of 5G technology, the tech industry is already looking ahead to the next big leap—6G. Promising speeds up to 100 times faster than 5G, 6G will revolutionize industries, improve communication, and unlock new
-

-

Quantum Computing: The Next Frontier in Technology
Read MoreIntroduction: The world of technology is constantly evolving, and one of the most exciting developments on the horizon is quantum computing. While traditional computers have revolutionized industries and transformed the way we live, quantum computers have the potential to solve complex problems that were previously
Key Areas of Cybersecurity Public Policy
National Security and Critical Infrastructure Protection
- Governments recognize that critical infrastructure, such as power grids, healthcare systems, and financial networks, are prime targets for cyberattacks. Public policy must prioritize the protection of these assets by implementing robust cybersecurity measures and encouraging public-private partnerships to share threat intelligence and best practices.
- Example: The U.S. Cybersecurity and Infrastructure Security Agency (CISA) works to enhance the security of critical infrastructure through collaboration with industry and government partners.
Data Privacy and Protection
- Public policy should ensure that individuals’ personal data is protected from unauthorized access, breaches, and misuse. Policies such as the General Data Protection Regulation (GDPR) in the European Union set stringent requirements for data protection, emphasizing the importance of user consent and the right to privacy.
- Governments must enforce data protection regulations and hold organizations accountable for compliance to safeguard citizens’ privacy.
Cybercrime and Law Enforcement
- Cybercrime is a growing threat that requires international cooperation and updated legal frameworks. Public policy should focus on enhancing law enforcement capabilities to investigate, prosecute, and prevent cybercrimes, including hacking, identity theft, and ransomware attacks.
- Example: The Council of Europe’s Convention on Cybercrime (Budapest Convention) provides a legal framework for international cooperation in combating cybercrime.
Cybersecurity Education and Workforce Development
- To address the growing demand for cybersecurity professionals, public policy should support education and training initiatives that equip individuals with the skills needed to protect digital systems. This includes investing in cybersecurity curricula at educational institutions and offering incentives for pursuing careers in cybersecurity.
- Example: National Cybersecurity Awareness Month in the U.S. promotes cybersecurity education and training across various sectors.
Research and Development
- Public policy should encourage innovation in cybersecurity by funding research and development (R&D) efforts. This includes developing new technologies, enhancing encryption methods, and exploring emerging threats such as quantum computing’s impact on cybersecurity.
- Governments can collaborate with academia and the private sector to drive R&D initiatives that strengthen national cybersecurity capabilities.
Global Cooperation and Standards
- Cyber threats are global in nature, requiring international cooperation and the establishment of common cybersecurity standards. Public policy should promote collaboration among nations to share intelligence, harmonize regulations, and respond collectively to cyber incidents.
- Example: The United Nations’ Group of Governmental Experts on Advancing Responsible State Behavior in Cyberspace works to build consensus on norms and principles for responsible state conduct in cyberspace.
Challenges in Cybersecurity Public Policy
- Balancing Security and Privacy: Ensuring cybersecurity often involves monitoring and surveillance, which can raise concerns about individual privacy. Public policy must carefully balance security measures with the protection of civil liberties.
- Rapid Technological Advancements: Technology evolves quickly, making it difficult for public policy to keep pace with new threats and vulnerabilities. Policymakers must remain agile and responsive to emerging cybersecurity challenges.
- International Jurisdiction and Enforcement: Cybercrime often transcends national borders, making it challenging to enforce laws and regulations. International cooperation is essential for effective enforcement and response to cyber threats.
Conclusion
Public policy plays a crucial role in shaping the cybersecurity landscape by establishing guidelines, regulations, and frameworks that protect digital assets and personal data. As cyber threats continue to evolve, policymakers must remain vigilant and proactive in addressing emerging challenges while fostering collaboration among governments, businesses, and individuals. Through well-crafted public policy, nations can enhance their cybersecurity resilience and ensure a safer digital future for all.