Endpoint Protection and Response (EPR)
In today’s complex threat landscape, endpoints such as laptops, desktops, mobile devices, and servers represent a critical entry point for cyberattacks. TechSecur3’s Endpoint Protection and Response (EPR) is designed to secure every endpoint in your organization, providing comprehensive protection from malware, ransomware, phishing, and advanced threats. Our EPR solution combines proactive endpoint security measures with advanced detection and response capabilities, ensuring that threats are neutralized before they can impact your business operations.
With TechSecur3’s EPR, you gain real-time visibility into endpoint activity, allowing for immediate detection of suspicious behaviors and rapid response to security incidents. This solution offers multi-layered protection and is built to adapt to the dynamic nature of modern cyber threats.
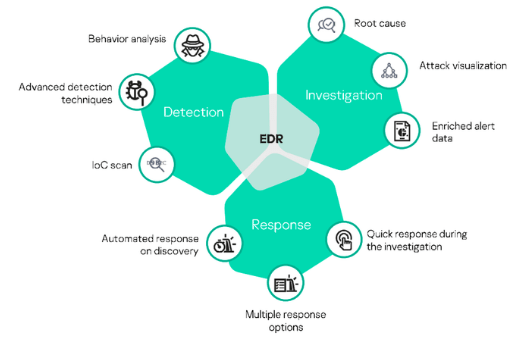
Key Features of TechSecur3’s Endpoint Protection and Response (EPR)
1. Advanced Malware and Threat Detection
TechSecur3’s EPR employs multiple detection techniques to identify both known and unknown threats, ensuring that even sophisticated attacks are caught and blocked.
- Behavior-Based Detection: Instead of relying solely on traditional signature-based methods, our EPR solution uses behavior-based analytics to detect anomalies and malicious activities on endpoints. This ensures that zero-day threats and advanced malware are identified, even if their signatures are unknown.
- AI and Machine Learning: Machine learning algorithms analyze patterns of activity on endpoints, learning to detect deviations that may indicate a threat. This enables proactive detection of emerging threats and rapid adaptation to new attack methods.
- Signature-Based Detection: Our EPR also includes signature-based scanning to quickly identify known malware and viruses, ensuring rapid response to common threats.
2. Endpoint Hardening and Prevention
Our EPR solution goes beyond detection by implementing preventive measures to harden endpoints against attacks.
- Application Control: By controlling which applications can run on your endpoints, TechSecur3 reduces the attack surface and blocks potentially harmful applications. Only whitelisted applications are permitted to run, ensuring security against unauthorized software.
- Device Control: We restrict access to removable devices (e.g., USB drives) and peripheral devices to prevent data theft, malware injection, and unauthorized data transfers.
- Exploit Prevention: TechSecur3’s EPR includes exploit prevention measures to protect endpoints from attacks that target software vulnerabilities, such as buffer overflow attacks or memory corruption exploits.
3. Endpoint Detection and Response (EDR)
TechSecur3’s EDR component enhances threat detection and response by continuously monitoring endpoint activity for suspicious behavior and providing deep forensic capabilities.
- Continuous Monitoring: Our EPR solution continuously monitors endpoint activity in real time, detecting potential threats as soon as they arise. This ensures that even the smallest anomaly is flagged for investigation.
- Automated Threat Containment: When a threat is detected, the EDR component can automatically isolate compromised endpoints from the network to prevent the spread of malware and reduce damage.
- Threat Hunting: TechSecur3 provides threat hunting capabilities that allow security teams to proactively search for hidden threats within endpoints. This helps identify and neutralize advanced threats before they cause harm.
4. Incident Response and Remediation
In the event of an attack, TechSecur3’s EPR enables rapid incident response and remediation to minimize the impact on your business.
- Real-Time Alerts: EPR sends real-time alerts to security teams when a threat is detected, providing detailed information about the nature of the threat, the affected endpoints, and the recommended response.
- Automated Remediation: Our EPR solution can automatically remove malicious files, terminate suspicious processes, and restore endpoints to a known-good state, ensuring that your endpoints are quickly returned to normal operations after an incident.
- Forensic Analysis: Following a security incident, TechSecur3 provides in-depth forensic analysis to determine how the attack occurred, what data was impacted, and how future incidents can be prevented.
5. Endpoint Encryption
To protect sensitive data stored on endpoints, TechSecur3’s EPR solution includes encryption capabilities that safeguard data, even in the event of device theft or loss.
- Full-Disk Encryption: TechSecur3 encrypts the entire contents of endpoint hard drives, ensuring that sensitive data is protected from unauthorized access, even if a device is physically compromised.
- File-Level Encryption: For added security, our EPR solution can encrypt specific files and folders, protecting critical business data and intellectual property at the file level.
- Remote Wipe Capabilities: If an endpoint is lost or stolen, TechSecur3 can remotely wipe the device to ensure that no sensitive data falls into the wrong hands.
6. Cloud-Based Management
TechSecur3’s EPR offers centralized cloud-based management, making it easy to manage and protect endpoints across multiple locations and devices.
- Unified Management Console: Our EPR solution provides a single pane of glass for managing endpoint security policies, monitoring threats, and responding to incidents across your entire organization.
- Scalability: TechSecur3’s cloud-based architecture allows our EPR solution to scale as your organization grows, ensuring that all of your endpoints are protected, no matter how large or distributed your environment becomes.
- Cross-Platform Support: Our EPR solution supports a wide variety of operating systems, including Windows, macOS, Linux, and mobile platforms, ensuring that every endpoint in your organization is secured.
Benefits of TechSecur3’s Endpoint Protection and Response (EPR)
1. Comprehensive Endpoint Security
TechSecur3’s EPR offers multi-layered security for endpoints, protecting against a wide range of threats, from common malware to advanced persistent threats (APTs). This ensures that your organization’s endpoints are fully protected against the most sophisticated cyberattacks.
2. Faster Threat Detection and Response
With real-time monitoring and automated response capabilities, TechSecur3’s EPR enables faster detection of threats and quicker incident response. This reduces the window of opportunity for attackers to cause damage, minimizing the impact on your business.
3. Reduced Attack Surface
By implementing endpoint hardening measures such as application and device control, TechSecur3’s EPR reduces the attack surface, making it more difficult for cybercriminals to exploit vulnerabilities.
4. Enhanced Visibility
TechSecur3’s EPR provides complete visibility into endpoint activity, helping your security team identify and investigate threats more effectively. This enhanced visibility allows for more informed decision-making when responding to incidents.
5. Simplified Management
With a centralized cloud-based management console, TechSecur3’s EPR makes it easy to manage endpoint security across your organization, even in remote or distributed environments. This simplifies administration while ensuring consistent security policies across all devices.
6. Compliance and Data Protection
TechSecur3’s EPR solution includes encryption and data protection measures that help your organization meet regulatory requirements and protect sensitive data. This reduces the risk of data breaches and ensures compliance with standards such as GDPR, HIPAA, and PCI DSS.
Why Choose TechSecur3 for Endpoint Protection and Response (EPR)?
TechSecur3 is dedicated to providing best-in-class endpoint security that meets the demands of today’s increasingly complex threat landscape. Our EPR solution combines cutting-edge technology with expert security management, delivering powerful protection for every endpoint in your organization.
- Experienced Security Professionals: TechSecur3’s team of cybersecurity experts helps design, implement, and manage your EPR solution, ensuring that your endpoints are protected against evolving threats.
- Innovative Security Tools: We leverage the latest in AI, machine learning, and behavior-based detection to provide proactive protection and rapid response to emerging cyber threats.
- Comprehensive Approach: TechSecur3’s EPR solution is more than just antivirus software; it’s a complete security strategy designed to secure endpoints from detection to response, ensuring that your business remains safe and secure.
With TechSecur3’s Endpoint Protection and Response, your organization can stay ahead of cyber threats, protecting endpoints from both known and unknown attacks while responding quickly to security incidents.